Enterprise Security Architecture: From access to audit
- 2. <Insert Picture Here> Enterprise Security Architecture: From access to audit Paul Andres Director, Enterprise Architecture
- 4. Changing Business Climate Challenges Our Customers Face… "In a time of accelerating turbulence, the valuation of a company will be strongly affected by how it executes change."
- 5. Today’s IT Challenges More Compliant Business • Increasing regulatory demands • Increasing privacy concerns • Business viability concerns More Agile Business More Secured Business • More accessibility for employees, • Organized crime customers and partners • Identity theft • Higher level of B2B integrations • Intellectual property theft • Faster reaction to changing requirements • Constant global threats
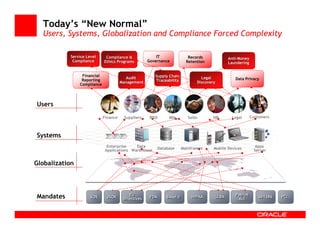
- 6. Today’s “New Normal” Users, Systems, Globalization and Compliance Forced Complexity Service Level Compliance & IT Records Anti-Money Anti- Compliance Ethics Programs Governance Retention Laundering Financial Supply Chain Audit Legal Data Privacy Reporting Traceability Management Discovery Compliance Users Finance Suppliers R&D Mfg Sales HR Legal Customers Systems Enterprise Data Database Mainframes Mobile Devices Apps Applications Warehouse Server Globalization EU Patriot Mandates SOX JSOX Directives FDA Basel II HIPAA GLBA Act SB1386 PCI…
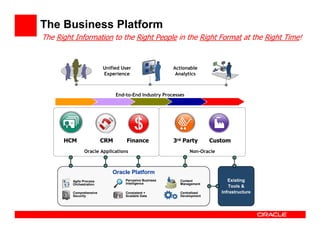
- 7. The Business Platform The Right Information to the Right People in the Right Format at the Right Time! Unified User Actionable Experience Analytics End-to-End Industry Processes HCM CRM Finance 3rd Party Custom Oracle Applications Non-Oracle Oracle Platform Agile Process Pervasive Business Content Existing Orchestration Intelligence Management Tools & Comprehensive Consistent + Centralized Infrastructure Security Scalable Data Development
- 8. Oracle is ‘Information Driven’ • Manage It… • Use It… • Share It… • Protect It…
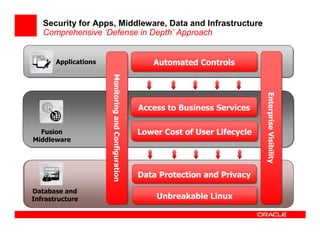
- 9. Security for Apps, Middleware, Data and Infrastructure Comprehensive ‘Defense in Depth’ Approach Applications Automated Controls Automated Controls Monitoring and Configuration Monitoring and Configuration Enterprise Visibility Enterprise Visibility Access to Business Services Access to Business Services Fusion Lower Cost of User Lifecycle Lower Cost of User Lifecycle Middleware Data Protection and Privacy Data Protection and Privacy Database and Infrastructure Unbreakable Linux Unbreakable Linux Copyright © 2008, Oracle and/or its affiliates. All rights reserved. 9
- 11. Oracle Enterprise Architecture Framework Methodology Business Architecture Governance Motivation Function Organization Drivers Models Products Mission Finance Reference Goals Strategy Services Roles Architectures Objectives Processes People EA Governance Strategy Applications Architecture Performance Principles Reference Architectures Functional Services Products Standards Risk Strategy General General General Components Security Policy Principles Industry Industry Industry Cost Integrity Business Continuity Capabilities Information Architecture Compliance Reference Architectures Entities Structures Portfolio Requirements Strategy Management Standards Models Design Principles Components Development Structures Data Quality Standards Test SLA’s Production Reference Technology Architecture Architectures Platform Services Products General Services Strategy SOA/ EDA Infrastructure Components Principles Cost Standards Data Management Development Security Management Version 2 (Draft)
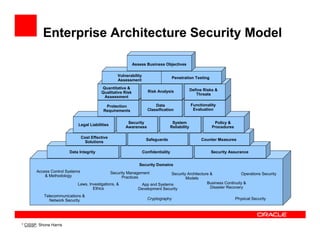
- 12. Enterprise Architecture Security Model Assess Business Objectives Vulnerability Penetration Testing Assessment Quantitative & Define Risks & Qualitative Risk Risk Analysis Threats Assessment Protection Data Functionality Requirements Classification Evaluation Security System Policy & Legal Liabilities Awareness Reliability Procedures Cost Effective Safeguards Counter Measures Solutions Data Integrity Confidentiality Security Assurance Security Domains Access Control Systems Security Management & Methodology Security Architecture & Operations Security Practices Models Laws, Investigations, & App and Systems Business Continuity & Ethics Development Security Disaster Recovery Telecommunications & Network Security Cryptography Physical Security * CISSP, Shone Harris
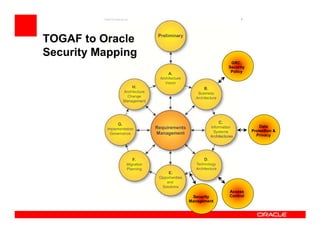
- 13. TOGAF to Oracle Security Mapping GRC, Security Policy Data Protection & Privacy Access Security Control Management
- 14. TOGAF 9
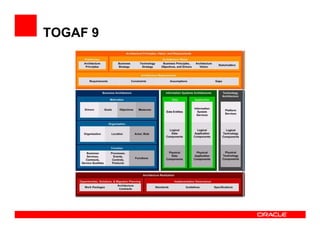
- 15. TOGAF 9
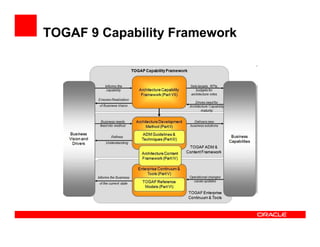
- 16. TOGAF 9 Capability Framework
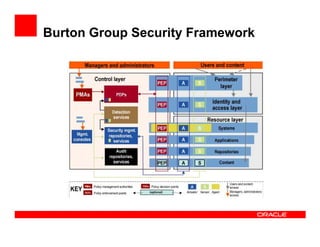
- 17. Burton Group Security Framework
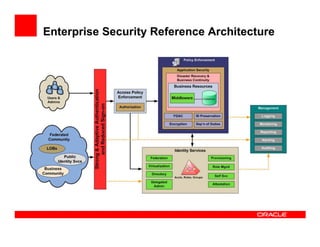
- 19. Enterprise Security Reference Architecture
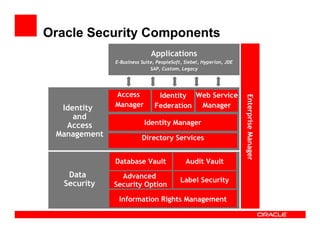
- 20. Oracle Security Components Applications E-Business Suite, PeopleSoft, Siebel, Hyperion, JDE SAP, Custom, Legacy Access Identity Web Service Enterprise Manager Identity Manager Federation Manager and Access Identity Manager Management Directory Services Database Vault Audit Vault Data Advanced Label Security Security Security Option Information Rights Management
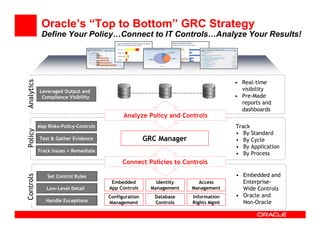
- 21. Oracle’s “Top to Bottom” GRC Strategy Analytics Define Your Policy…Connect to IT Controls…Analyze Your Results! • Real-time Leveraged Output and visibility Compliance Visibility • Pre-Made reports and dashboards Analyze Policy and Controls Map Risks-Policy-Controls Track Policy • By Standard Test & Gather Evidence GRC Manager • By Cycle • By Application Track Issues + Remediate • By Process Connect Policies to Controls • Embedded and Controls Set Control Rules Embedded Identity Access Enterprise- Low-Level Detail App Controls Management Management Wide Controls Configuration Database Information • Oracle and Handle Exceptions Management Controls Rights Mgmt Non-Oracle
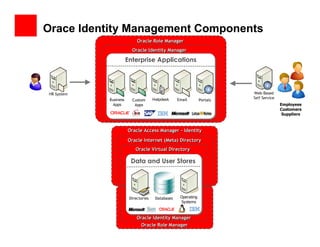
- 22. Orace Identity Management Components Oracle Role Manager Oracle Identity Manager Enterprise Applications Basic Authentication / Course-Grained Authorization / Audit / User Administration Business Custom Helpdesk Email Portals Apps Apps Employees Customers Suppliers Oracle Access Manager - Identity Oracle Internet (Meta) Directory Oracle Virtual Directory Data and User Stores Directories Databases Operating Systems Oracle Identity Manager Oracle Role Manager
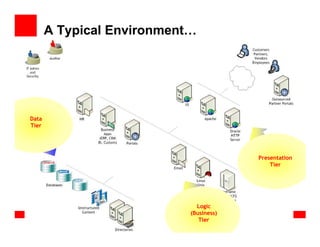
- 23. A Typical Environment… Data Tier Presentation Tier Logic (Business) Tier
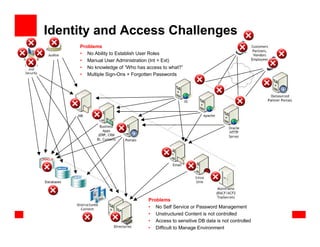
- 24. Identity and Access Challenges Problems • No Ability to Establish User Roles • Manual User Administration (Int + Ext) • No knowledge of “Who has access to what?” • Multiple Sign-Ons + Forgotten Passwords Problems • No Self Service or Password Management • Unstructured Content is not controlled • Access to sensitive DB data is not controlled • Difficult to Manage Environment
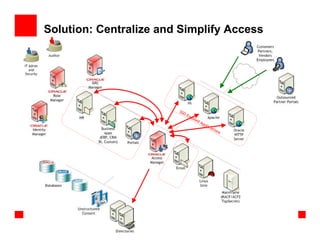
- 25. Solution: Centralize and Simplify Access SSO En ab led Ap pli cat ion s
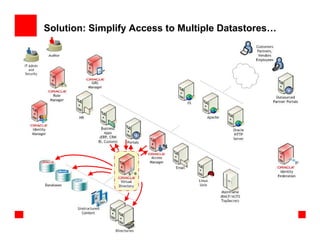
- 26. Solution: Simplify Access to Multiple Datastores…
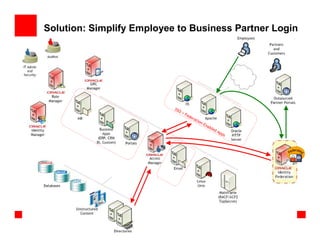
- 27. Solution: Simplify Employee to Business Partner Login SSO +F ed e rat i on -En ab l ed Ap p s
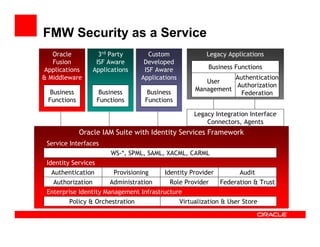
- 28. FMW Security as a Service Oracle 3rd Party Custom Legacy Applications Fusion ISF Aware Developed Applications Applications ISF Aware Business Functions & Middleware Applications Authentication User Authorization Business Business Business Management Federation Functions Functions Functions Legacy Integration Interface Connectors, Agents Oracle IAM Suite with Identity Services Framework Service Interfaces WS-*, SPML, SAML, XACML, CARML Identity Services Authentication Provisioning Identity Provider Audit Authorization Administration Role Provider Federation & Trust Enterprise Identity Management Infrastructure Policy & Orchestration Virtualization & User Store
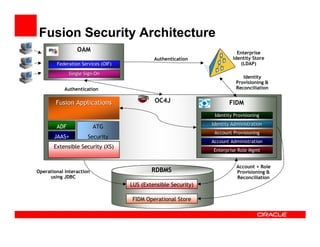
- 29. Fusion Security Architecture OAM Enterprise Authentication Identity Store Federation Services (OIF) (LDAP) Single Sign-On Sign- Identity Provisioning & Authentication Reconciliation Fusion Applications OC4J FIDM Identity Provisioning Identity Administration ADF ATG Account Provisioning JAAS+ Security Account Administration Extensible Security (XS) Enterprise Role Mgmt Account + Role Operational Interaction RDBMS Provisioning & using JDBC Reconciliation LUS (Extensible Security) FIDM Operational Store
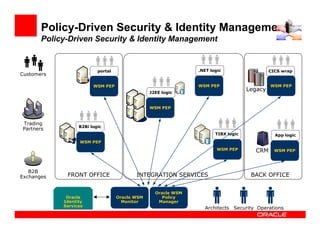
- 30. Policy-Driven Security & Identity Management Policy-Driven Security & Identity Management portal .NET logic CICS wrap Customers WSM PEP WSM PEP WSM PEP J2EE logic Legacy WSM PEP Trading B2Bi logic Partners TIBX logic App logic WSM PEP WSM PEP CRM WSM PEP B2B Exchanges FRONT OFFICE INTEGRATION SERVICES BACK OFFICE Oracle WSM Oracle Oracle WSM Policy Identity Monitor Manager Services Architects Security Operations
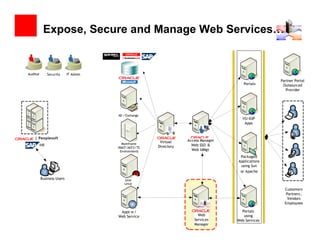
- 31. Expose, Secure and Manage Web Services… Auditor Security IT Admin Partner Portal Portals Outsourced Provider AD / Exchange IIS/ASP Apps | Peoplesoft Virtual Access Manager HR Mainframe Web SSO & (RACF /ACF2/TS Directory Environment) Web IdMgt Packaged Applications using Sun or Apache ` Business Users Unix Linux Customers Partners , Vendors Employees Apps w / Portals Web Service Web using Services Web Services Manager
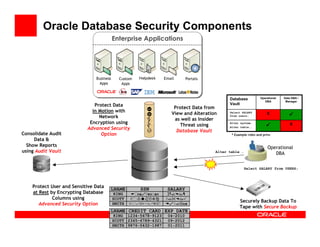
- 32. Oracle Database Security Components Enterprise Applications Business Custom Helpdesk Email Portals Apps Apps Database Operational Data DBA / DBA Manager Protect Data Vault Protect Data from in Motion with View and Alteration Select SALARY X Network from users; as well as Insider Encryption using Alter system. X Threat using Alter table.. Advanced Security 5 Database Vault Consolidate Audit Option * Example roles and privs Data & Show Reports Operational using Audit Vault Alter table …. DBA Select SALARY from USERS; Protect User and Sensitive Data LNAME SSN SALARY at Rest by Encrypting Database KING 123-45-6789 $125,000 Columns using SCOTT 987-65-4321 $229,500 Securely Backup Data To Advanced Security Option SMITH 345-67-8912 $ 53,700 Tape with Secure Backup LNAME CREDIT_CARD EXP_DATE KING 1234-5678-9123 04-2010 SCOTT 2345-6789-4321 09-2012 SMITH 9876-5432-1987 01-2011
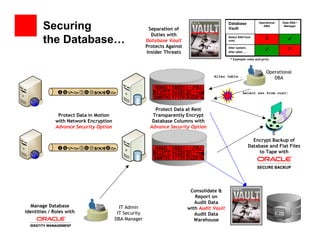
- 33. Securing Database Operational Data DBA / DBA Manager Separation of Vault Duties with the Database… Database Vault Protects Against Select SSN from cust; X Alter system.. X Insider Threats Alter table …. * Example roles and privs Operational Alter table …. DBA KING 18031 KING, 18031, $1,800 5 0 SCOTT 14220 Select ssn from cust; SMITH 17170 ִ Protect Data at Rest Protect Data in Motion Transparently Encrypt with Network Encryption Database Columns with Advance Security Option Advance Security Option Encrypt Backup of KING, 18031, $1,800 Database and Flat Files 5 0 KING 18031 SCOTT 14220 to Tape with SMITH 17170 ִ Consolidate & Report on Audit Data Manage Database IT Admin with Audit Vault Identities / Roles with IT Security Audit Data DBA Manager Warehouse
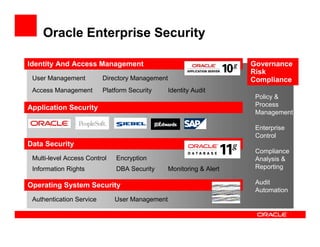
- 35. Oracle Enterprise Security Identity And Access Management Governance Risk User Management Directory Management Compliance Access Management Platform Security Identity Audit Policy & Process Application Security Management Enterprise Control Data Security Compliance Multi-level Access Control Encryption Analysis & Information Rights DBA Security Monitoring & Alert Reporting Operating System Security Audit Automation Authentication Service User Management