Reimagining security through the power of convergence at Google Cloud Security Summit 2024

Sunil Potti
VP/GM, Google Cloud Security
To keep pace with modern threats, organizations large and small need to take a hard look at their security tooling and determine how they can adapt to accelerate step function change. And while this may seem daunting, Google Cloud Security can help you make sure it doesn't have to be.
To truly elevate security, we believe in the power of simplicity. Instead of adding new, siloed products to address specific threats, we need to reduce the number of moving parts — a more effective approach that converges existing capabilities and infuses them with AI and frontline threat intelligence, to enable the next level of proactive defense.
At today’s Google Cloud Security Summit 2024, we're focusing on this crucial theme, reimagining cybersecurity through the power of convergence.
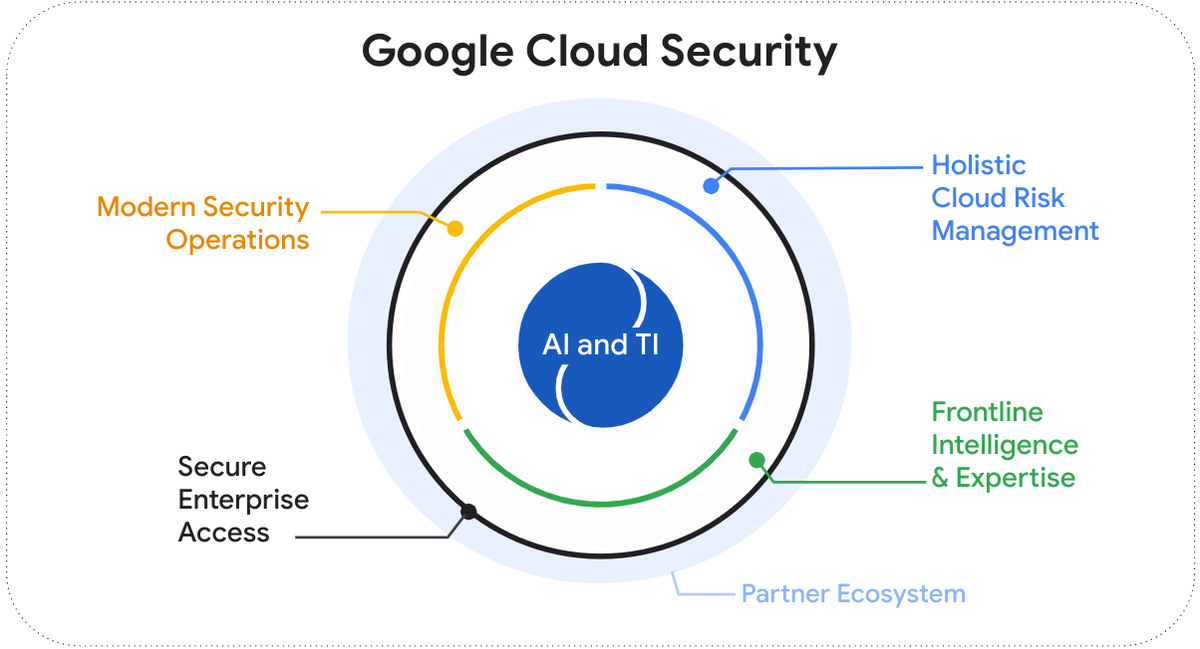
In our product and solution portfolio, we intentionally chose strategic capabilities that can have the largest impact on your security posture and programs — a platform to drive the core security functions of detection, investigation, and response, risk management for where business critical applications and data increasingly live, essential frontline expertise and intelligence on current threats, and the modern enterprise access platform. These areas become the anchor points for further convergence. Here’s what convergence looks like today across our Security portfolio:
-
Modern security operations: Our modern SecOps platform goes beyond replacing legacy SIEM. It unifies SIEM, SOAR, and Attack Surface Management to proactively detect and respond to threats.
-
Frontline intelligence and expertise: We harness the power of human expertise in incident response, red teaming, and threat hunting to help organizations before, during, and after an attack.
-
Holistic cloud risk management: Our multicloud security and risk management solution not only brings together capabilities to protect code, identities, and data across multiple clouds, but accelerates operational convergence between cloud security and enterprise SecOps to streamline risk remediation.
-
Secure enterprise access: Our approach leverages the existing Chrome Enterprise footprint, activating hundreds of millions of devices for non-invasive endpoint threat detection, data protection, and Zero Trust access.
-
AI and threat intelligence: We power structurally smarter security across all of these domains by infusing threat intelligence.

Convergence in action
The benefits of convergence also accrue from intentional, targeted integrations with strategic partners. Working with partners helps us mesh with the security ecosystems our customers have built and unlock opportunities to achieve a significant set of outcomes across a much larger security surface area.
Let’s look at how we’re continuing to evolve our converged portfolio.
Google Security Operations
The SIEM market is undergoing tectonic shifts, causing security operations leaders to rethink their platforms and approach. Google Security Operations customers such as Etsy are rising to the occasion, making significant changes in both the technology they use and the way they think about SecOps.
“This is our chance to reset, [have a] clean slate,” said Manan Doshi, senior security engineer, Etsy.
From approaching their Google Security Operations migration as a hack-a-thon project, to focusing on new processes that helped them build a stronger foundation, to utilizing AI to add uniformity and consistency across their team, Etsy has shown how our security operations platform can help organizations modernize their security and prepare for the future. Join their Security Summit session to learn more about their migration and SecOps modernization best practices.
Apex Fintech Solutions is also reimagining their Security Operations Center with the power of Gemini and generative AI.
“No longer do we have our analysts having to write regular expressions that could take anywhere from 30 minutes to an hour — Gemini can do it within a matter of seconds,” said Hector Peña, senior information security director, Apex Fintech Solutions.
You can hear more about the benefits Apex Fintech Solutions has realized with Gemini in Security Operations at their Security Summit session.
Mandiant services
Adding to Mandiant threat hunting products and services available today, we are announcing Mandiant Custom Threat Hunt. This point-in-time threat hunt can complement managed detection and response services, or can supplement an in-house threat hunting program, to help organizations uncover ongoing and past threat actor activity in their environment, while improving their ability to effectively detect future threats.
Organizations that have benefited from Mandiant’s custom threat hunts have often experienced at least one of the following security concerns in the weeks or months before using the service:
-
Increased targeting by specific threat actors known to operate in your industry or vertical
-
Implementation of new technologies, cloud platforms, and SaaS solutions
-
Business partners and supply chain providers impacted by an incident or breach
-
To assess and hunt across newly acquired security tools, log sources, and controls
-
Planned or recent mergers and acquisitions
Our latest Defender's Advantage Cyber Snapshot report provides insights into cyber defense topics based on Mandiant frontline observations and real-world experiences. It covers the benefits of deploying a security deception strategy, the critical role of insider threat penetration testing, how to effectively assess web-based foundation models, and a guide to SIEM migration.
Security Command Center
Security Command Center (SCC), our cloud-native application protection platform (CNAPP) solution, has added new capabilities to surface toxic combinations - security issues that create unacceptable risks when they occur together.
SCC finds toxic combinations using a unique approach: virtual red teaming. It continuously simulates a determined attacker who attempts to infiltrate cloud defenses and reach high-value assets, trying millions of attack permutations against a digital twin model of your cloud environment to find possible attack paths. Unlike other CNAPPs that rely on generic, vendor-developed rules that look only for known issues, SCC’s virtual red team can find toxic combinations that have never been seen before, and help our customers respond to cloud risks they did not know about. Discovery of toxic combinations is now in preview.
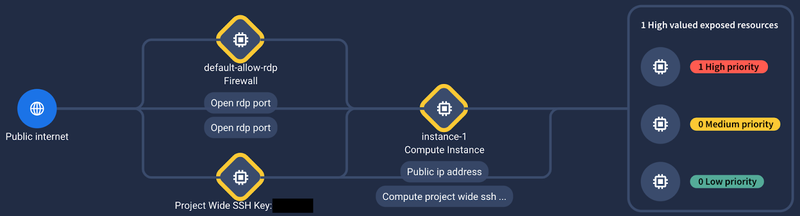

Visualization of a toxic combination discovered by SCC virtual red teaming
Security Command Center has also broadened its multicloud cloud infrastructure entitlement management (CIEM) capabilities to help customers maintain a least privilege access model. New generally available capabilities in SCC support Entra ID (Azure AD) and Okta identities on Google Cloud, and AWS IAM identities for AWS.
Security in Google Cloud
We continue to add new controls and capabilities to help strengthen your security posture and ensure compliance in your Google Cloud environment. Today at the Summit, we’re announcing or updating the following:
For Identity and Access Management:
-
Privileged Access Manager (PAM): Now in preview, PAM helps you enforce the principle of least privilege by enabling just-in-time, time-bound, and approval-based access elevations for high-privilege users.
-
Principal Access Boundary (PAB): Also in preview, this identity-centered control allows security administrators to define authorized resource sets for principals, regardless of existing IAM policies.
-
Certificate-Based Access (CBA): Now generally available, certificate-based access uses mutual TLS (mTLS) to ensure that user credentials are bound to a device certificate before granting access.
-
Workforce Identity Federation: Now generally available, support for Microsoft Entra ID enables users to access Google BigQuery from Microsoft Power BI with Single-Sign-On. Using a syncless, attribute-based access control capability, Microsoft Entra ID groups can be used to authorize access to Google BigQuery without requiring users or groups provisioned in Google Cloud.
-
VPC Service Controls (VPC-SC) with Private IP support: Now generally available, new private IP support in VPC-SC allows you to authorize traffic from specific internal networks or on-premises environments to protected cloud resources.
For Data Security:
-
New Confidential VM options: Now in preview, new Confidential VM options can help protect your data and applications in use with hardware-based memory encryption. The general availability of AMD SEV-SNP on N2D machines and preview on C3D instances adds strong memory integrity, encrypted register state, and hardware-rooted remote attestation, further strengthening data confidentiality and integrity.
-
Key Access Justifications (KAJ) for Cloud HSM: Now available in preview with Assured Workloads, KAJ now supports CloudHSM, providing access transparency and justifications for Cloud HSM-based keys.
For Network Security:
-
Cloud Armor: New capabilities for Cloud Armor Enterprise add adaptive protection at a granular-host level (now generally available), and support for regional Internal Application Load Balancers and IP address groups (in preview). These can help you create more efficient, regionally-scoped Cloud Armor security policies.
-
Cloud Next-Generation Firewall: Recently released, Cloud NGFW Enterprise showed impressive detection rates against known vulnerabilities and malware samples in third-party independent testing by Miercom and SecureIQ.
For Regulated Cloud:
- New Sovereign Controls by Partners: We recently announced the general availability of new Sovereign Controls by Partners control packages in two regions. In Italy, Sovereign Controls by PSN is specifically targeted to the Italian public sector, providing tools, features, and controls to secure sensitive government workloads. In Saudi Arabia, Sovereign Controls by CNTXT adds partner-operated controls to Google Cloud's Class C-certified infrastructure for organizations operating a Google Cloud environment in the Kingdom.
- Assured Workloads updates: The new Compliance Updates feature, now in preview, allows you to evaluate if your current Assured Workloads folder configuration differs from the latest available control package configuration, and enables you to upgrade previously created folders.
Chrome Enterprise
Chrome Enterprise Premium brings together the most popular and trusted enterprise browser with Google’s advanced security capabilities, including threat and data protection, Zero Trust access controls, enterprise policy controls, and security insights and reporting. New capabilities in Chrome Enterprise Premium enable you to:
-
Get started quickly with pay-as-you-go pricing
-
Protect your data with watermarking
-
Gain greater visibility into browsing activity with URL filtering for browser history
-
View Chrome Security Insights for a more nuanced understanding of threats
Learn more at Google Cloud Security Summit
When you make Google part of your security team, you can embrace the power of convergence and simplify security. Learn more about our announcements by attending the Google Cloud Security Summit, which runs today and on-demand afterwards.



