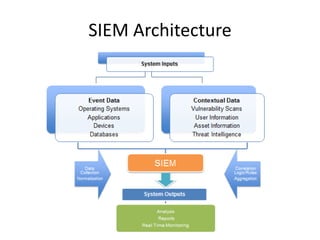
SIEM Architecture
- 1. SIEM Architecture By Nishanth Kumar Pathi
- 2. Nishanth Kumar Pathi • Information Security Consultant • null – moderator • OWASP Contributor • @nishanthkumarp • http://nishanth.co.in
- 5. Problem Statement • Which events should be gathered ? • How we manage the vast amount of logs and information • What and How should we parse, normalize and time-correction ? • How should the events be stored ? • Identify data breach internal or external • Mitigate cyber attacks. • Meet Compliance Requirements.
- 6. What is SIEM • Security Incident Event Management • Real time monitoring of Servers, Network Devices. • Correlation of Events • Analysis and reporting of Security Incidents. • Threat Intelligence • Long term storage
- 7. Evolution • SIM – System* Information Management • SEM - Security Event Management • NBA – Network Based Analysis • Log Management – Log file capture & Storage • SIEM - SIM & SEM
- 9. What it can collect ?
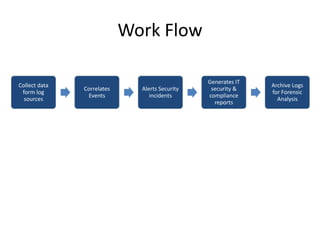
- 10. Work Flow Collect data form log sources Correlates Events Alerts Security incidents Generates IT security & compliance reports Archive Logs for Forensic Analysis
- 12. Dashboard
- 13. Implementation
- 14. Self Hosted , Self Managed
- 15. Cloud Hosted , Self Managed
- 16. Hybrid Model , Jointly Managed
- 17. Why SIEM Implementation Fails ? • Lack of Planning • Faulty Deployment Strategies. • Operational Knowledge
- 18. Any Questions ?
- 19. Nishanth Kumar Pathi • Information Security Consultant • null – moderator • OWASP Contributor • @nishanthkumarp • http://nishanth.co.in