Detection of malicious consumer interest packet with dynamic threshold values
- Published
- Accepted
- Received
- Academic Editor
- Vicente Alarcon-Aquino
- Subject Areas
- Computer Networks and Communications, Emerging Technologies, Security and Privacy
- Keywords
- Content poisoning attacks, Named data networking, Malicious consumer interest packet, Mitigation techniques, Dynamic threshold
- Copyright
- © 2021 Qureshi et al.
- Licence
- This is an open access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, reproduction and adaptation in any medium and for any purpose provided that it is properly attributed. For attribution, the original author(s), title, publication source (PeerJ Computer Science) and either DOI or URL of the article must be cited.
- Cite this article
- 2021. Detection of malicious consumer interest packet with dynamic threshold values. PeerJ Computer Science 7:e435 https://doi.org/10.7717/peerj-cs.435
Abstract
As a promising next-generation network architecture, named data networking (NDN) supports name-based routing and in-network caching to retrieve content in an efficient, fast, and reliable manner. Most of the studies on NDN have proposed innovative and efficient caching mechanisms and retrieval of content via efficient routing. However, very few studies have targeted addressing the vulnerabilities in NDN architecture, which a malicious node can exploit to perform a content poisoning attack (CPA). This potentially results in polluting the in-network caches, the routing of content, and consequently isolates the legitimate content in the network. In the past, several efforts have been made to propose the mitigation strategies for the content poisoning attack, but to the best of our knowledge, no specific work has been done to address an emerging attack-surface in NDN, which we call an interest flooding attack. Handling this attack-surface can potentially make content poisoning attack mitigation schemes more effective, secure, and robust. Hence, in this article, we propose the addition of a security mechanism in the CPA mitigation scheme that is, Name-Key Based Forwarding and Multipath Forwarding Based Inband Probe, in which we block the malicious face of compromised consumers by monitoring the Cache-Miss Ratio values and the Queue Capacity at the Edge Routers. The malicious face is blocked when the cache-miss ratio hits the threshold value, which is adjusted dynamically through monitoring the cache-miss ratio and queue capacity values. The experimental results show that we are successful in mitigating the vulnerability of the CPA mitigation scheme by detecting and blocking the flooding interface, at the cost of very little verification overhead at the NDN Routers.
Introduction
Named Data Networking (NDN) is a well-known and well-researched architecture for the next generation of the Internet, based on a data-centric approach. While the legacy network is based on a host-centric system, the NDN architecture has changed the Internet’s communication model altogether (Jacobson et al., 2009). It allows the distribution of data that can be acquired from any content router from the network. A content provider can produce the data in advance and place it as auxiliary storage that can be accessed by any consumer anytime, even if the producer gets offline. A producer does not have to be online, and a consumer does not have to be connected to the producer to fetch the data; Instead, the consumer can acquire data through in-networking caches. While NDN increases content availability in the network via in-network caching, the integrity of content becomes critical, given NDN’s nature (Tarkoma, Ain & Visala, 2009). Hence, NDN opens several security-related issues that are not relevant to the legacy network communication. It includes some new types of data integrity attacks where a malicious or compromised node provides a corrupted copy of the content. These issues are often ignored in NDN-related communication and caching mechanisms and are our main focus in the article.
One of the most critical attack vectors in NDN is the Content Poisoning Attack. The attacker compromises the Content Router (CR), and this compromised CR sends a reply to the legit request with totally bogus or corrupted content. This poisoned content pollutes the in-network caches of intermediate NDN routers and thus deprives the consumers of the requested content’s legitimate copy. Hu et al. (2018) proposed a comprehensive scheme to mitigate the Content Poisoning Attack (CPA). A special interest packet is generated by the consumer, which contains the hash of the poisoned data. This article is all about the identification and mitigation of security flaws that can be exploited by the attacker during this CPA mitigation process.
The research problem lies in the CPA mitigation scheme proposed by Hu et al. (2018). A consumer with malicious intent can flood the network with the Interest packet containing the hash digest of legit or un-poisoned data. This hash is stored in its exclude filter field. During CPA mitigation, this packet can flood the network, which will enable multipath forwarding and on-demand verification of hash at the router. This flooding attack can severely affect the throughput of the network or even cause a denial of service for other legitimate consumers. Therefore, it is essential to mitigate and add this additional security feature along with CPA mitigation (Qureshi & Anjum, 2020).
In this article, we proposed a scheme to detect the flooding attack generated by the compromised Consumer. A satisfaction test is performed to check if the excluded interest packet is non-existent in the cache or a legit packet. If the cache miss ratio (of the excluded interest packet) reaches the threshold value, it is considered an attack. A lightweight parameter is added to the Content Store data structure, which stores cache miss counter value. This value is compared with the specified threshold value. When the cache miss counter reaches near that threshold value, an event is raised that blocks the incoming malicious face. Also, in our scheme, we made the threshold value adaptable. At first, the initial threshold value is calculated by taking the total buffer size and divided it by the verification rate. The proposed idea is that when cache miss ratio avg crosses 50%, and queue capacity saturates, the threshold value is reduced to half. This process continues until the value is thrashed to one.
The articles’s main contribution is the addition of a security feature that fills up the attack surface that can be exploited by the malicious consumer. Our contributions are:
-
Adjustment of the threshold value dynamically by monitoring the cache-miss ratio value and queue capacity.
-
Detection and mitigation of the flooding attack of special interest packets generated while mitigating the content poisoning attack.
Further, this article is organized into five sections; the second section emphasizes the literature review and related work. The third section is the proposed approach, and in the fourth section, experiments and results are highlighted along with the conclusion in the fifth section.
Proposed Approach
Introduction
The name-key based forwarding and Multipath forwarding based Inband probe is a very comprehensive scheme for mitigation of the CPA. It fills most of the attack surfaces regarding the Content Poisoning Attack. However, with the advent of the NDN architecture’s structural changes, it has induced a new attack vector that can be exploited by the adversary. With this attack, the whole system can collapse. So it is very crucial to highlight this aspect. One of the important attack vectors that have emerged with this technique is the flooding of the reissued Interest Packet containing the excluded filter field. It is the leading research contribution of this article. A consumer with malicious intent can flood the network with interest containing the hash digest of legit or unpoisoned data in its exclude field, which can flood the network and enable multipath. It can harm the throughput of the network or even can cause DDoS. Based on the research gap mention in the previous section, this article has formulated the following research questions: What will be the mechanism to detect the attack initiated by consumers with malicious intent? What will be the parameters that will mitigate the malicious consumers’ reissued interest packet flooding attack? So it’s essential to mitigate and add this additional security feature in this CPA Mitigation technique.
Detection of malicious consumer interest packet with excluded filter field
During the CPA, the reissued Interest Packet by the consumer stores the hash of the poisoned data in the excluded filter field but a compromised consumer can also store the hash of and un-poisoned data has in the same field. Consequently, It will result in a cache miss. The on-demand signature verification at the router will also be enabled during this process, consuming a lot of router processing power. When a consumer with malicious intent bombards these excluded Interest packets, although they get discarded at the next router upon verification, it will drastically increase the router’s processing overhead. Other legitimate consumers will face a denial of service from this router. This attack vector should be taken into account, and a mitigation strategy should be devised for such attacks. This way, the process of CPA mitigation will be severely affected. The block diagram of the flooding scenario is elaborated in Fig. 1. The block diagram depicts the scenario of the flooding attack of Interest Packet with excluded filter. The first block shows that the consumer generates the normal Interest packet. Then a decision is taken in the next block that whether it is a normal Interest packet or an Interest packet with an excluded filter field. In case it is a normal Interest packet, it is directed towards normal NDN operations; otherwise, it is passed to the next module of On-Demand Signature Verification. Here signature verification is performed against PPKD in the Content Store. If validation fails, this packet is discarded; otherwise, it gets purged from the router’s CS. In the case of poisoned Data is found in the CS, the normal process is initiated, and content poisoning mitigation will commence. When a consumer is compromised, and it starts flooding the NDN Network with the excluded filter enabled Interest packet, it will trigger On-Demand Signature verification for each bogus packet, and the next NDN router will get saturated. The queue will be occupied, and after a while, there will be less space for the legitimate excluded filter Interest packet. It will hamper the CPA Mitigation mechanism badly. So this scenario is considered an attack and needs mitigation.
Figure 1: Detection of flooding attack during content poisoning attack mitigation.
Mitigation of flooding attack
In this article, a reactive approach is proposed to mitigate this attack. A virtual queue is utilized in NDN Routers for incoming reissued Interest packets from the consumers. FIFO (FCFS) queue is shared among all the incoming faces for reissued interest packets. It is a temporary place holder for these packets until they get verified. The allotted memory for the transmitting packets should be different from the one used for caching. If the same CS is used to transmit packets and data chunk, then the CS will be congested with the data chunks that are waiting to be satisfied by the pending Interest packets. To prevent the Malicious consumer from sending a fake “excluded Interest packet,” a satisfaction test is performed to check if the excluded interest packet is non-existent in the cache or a legit packet in the cache. In case a cache miss (of the excluded interest packet) occurs, and the ratio reaches near the threshold value, that is, it is set by the operator, it is considered an attack. On-demand verification at the router is not enabled unless there is a cache hit of the excluded interest packet; this will reduce the overhead of content verification at each data packet’s router. However, in case of a cache miss, this excluded interest packet is discarded. Still, if a consumer with malicious intent floods the edge router with the fake interest packet with the excludes filter, it will degrade that particular edge router’s performance. The NDN-router service manager at the NDN Router, especially at the edge of the network in the consumer domain, maintains the stats and looks at them. The router will drop the future reissued interests coming from this face with the excluded data packet as it is considered a malicious consumer upon hitting the threshold value. It will be done temporarily and delisted at the discretion of the network operator. A new lightweight parameter is added in the CS Data Structure to retain the cache miss counter of invalid reissued Interest packet with excluded filter field. This value is compared with the threshold value. The Block diagram can show the birds-eye view of this proposed mechanism in Fig. 2.
Figure 2: Mitigation of flooding attack.
We have introduced a block of the proposed approach. The reissued Interest packet upon several caches misses, and hitting the specified threshold value will trigger an event and blocks this malicious face. On the next iteration, this reissued packet from the malicious consumer face will be blocked. In Algorithm 1 (Fig. 3) PPKD, ContentName, nonce, incoming face, excluded filter field value, Threshold value, and cache miss counter value is passed as an argument. At statement 1, the hash comparison is performed and if the result is a cache miss then the cache miss counter value gets incremented. If that value reaches the threshold value then the event to block that specific malicious incoming face gets triggered. In case the result is a cache hit then the normal NDN communication process will commence.
Figure 3: Detection and mitigation of flooding attack of reissued interest packet.
Dynamic threshold value
This approach helps the Network Operators set up the threshold value automatically during the special interest packet flooding attack by a malicious consumer. This approach aims to select the threshold value in an automated fashion based on the statistical monitoring of buffer capacity and cache miss ratio. In this approach, a Network Management software continuously monitors the cache miss ratio and buffer capacity when a special interest packet is initiated. When the cache miss ratio average over a while results in a buffer overflow, the threshold value is thrashed to half. This process continues unless the threshold value becomes 1. This mechanism is elaborated in Algorithm 2 (Fig. 4). At this stage, the incoming face causing the flooding attack will get blocked till the particular timeout.
(1) (2)Network Management Software will continuously monitor the Cache_Miss_Ratio and Buffer Size of the queue.
Figure 4: Dynamic threshold value.
Benefits of dynamic threshold values over static threshold values
The mitigation of flooding attack of special interest packets works on two approaches, first one uses the static threshold values which is set by network operators during the router initial configuration. The second approach is the dynamic approach, in which the threshold value is adjusted adaptively by monitoring the Queue size and Cache Miss Ratio value.
Experimental Results
Simulation environment
For proof of concept and to run this scenario, a custom-built NDN Simulator is developed in C# language in Visual Studio 2019. The network parameters used in simulation scenarios are mentioned in Table 4.
| Parameter | Default value |
|---|---|
| Request rate | 100 Interests/second/consumer |
| (interest with exclude parameter) | |
| Max queue length | 500 (Experiment 1 and Experiment 2) |
| 1,000 (Experiment 3 and Experiment 4) | |
| Verification of interest packet | 25 Interest/second |
| No. of malicious consumers | 1 (Experiment 1 and Experiment 2) |
| 2 (Experiment 3 and Experiment 4) | |
| Threshold value | x |
Network topology
Scenario 1: one malicious consumer
In scenario 1, our simulations’ network topology consists of two routes from the consumer to the producer. Two paths routes that are used in this scenario are 0-1-2-4-6-7-8 and 0-1-3-5-7-8; these paths are between the consumer and a producer (Spring et al., 2004). In this scenario, it is evident that consumers with malicious intent can flood the network with unwanted interest packets with excluded fields occupied by the non-malicious or legit payload. If not mitigated at the edge router, all the routers will enable the on-demand verification, and this way, router performance will degrade with time. This problem can be mitigated by enabling a mechanism at edge routers of NDN and setting a threshold value that if it hits this value, block that interface through which these malicious excluded interest packets are coming. This way, the rest of the network will be safe from acquiring this malicious packet from consumers, and ultimately the performance of the intermediate routers will not be degraded. So to handle this issue Network Manager at NDN Edge Router enables this mechanism in which malicious interest packet with exclude field is dropped in case of a cache miss, and upon hitting the threshold value, the interface from which these excluded interest packets are received is blocked and added to the delist data structure. The timeout to get out of this delist data structure is at the desecration of the network operator.
Scenario 2: two malicious consumers
In scenario 2, our simulations’ network topology consists of two routes from two consumers (i.e., Consumer 1 and Consumer 2) of the same domain to the producer via Router 8 (edge router). The routes that are used in this scenario is 0-1-2-4-6-7-8 and 0-1-3-5-7-8; these paths are between the consumer and a producer (Spring et al., 2004). The main thing to note in this scenario is that Consumer 1 and Consumer 2 are in the same domain. Router 8, the virtual queue for Incoming Reissued Interests, is shared between these two consumers. The Queuing mechanism used in this scenario is FIFO. There are two consumers with malicious intent in this scenario and can flood the network with unwanted interest packets with excluded fields occupied by the non-malicious or legit payload. If not mitigated at the edge router, the virtual queues will be fully occupied for the legit reissued interest packet, and consequently, packets will drop. This problem can be mitigated by enabling a mechanism at edge routers of NDN and setting a threshold value that if it hits this value, block that interface through which these malicious excluded interest packets arrive. This way, the rest of the network will be safe from acquiring this malicious packet from consumers, and ultimately the performance of the intermediate routers will not be degraded.
Experiments and result
Experiment 1 (Scenario 1): with no threshold values
In this experiment as shown in Fig. 5, we have calculated the cache miss ratio of the interest packet containing the exclude filter and compared it with the Queue Length. Upon flooding the router with a fake interest packet, the verification process takes time, and meanwhile, the queue of interest packets will start increasing. After every second, 25% fake packet will drop, and 75% will be added to the queue. Initially, no threshold value is set. After some time, congestion at the router’s incoming interest packet queue will occur, resulting in a drop of other future packets at this router.
Figure 5: Flooding attack with no threshold value and with one malicious consumer.
Experiment 2 (Scenario 1): with threshold values
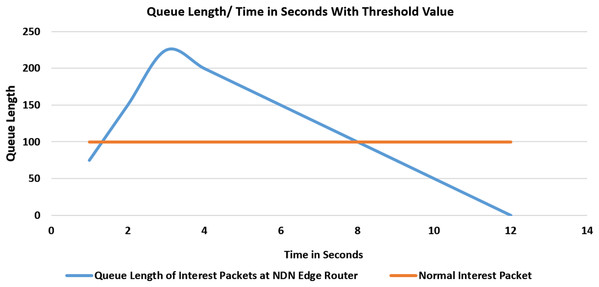
In the second experiment as shown in Fig. 6, our proposed scheme is enabled at the edge routers in Network Management software. After several cache misses and upon hitting the threshold value to 3 according to the simulation settings, it will block the incoming face of the consumer, and further, no more interest packets will be received from this malicious consumer face. After hitting the specified threshold value, the face is blocked and fake packets begin to drop from the queue. At 12 s the queue will be empty and the router is no more saturated.
Figure 6: Flooding attack with threshold value and with one malicious consumer.
Experiment 3 (Scenario 2): with no threshold values
In the third experiment as shown in Fig. 7, Consumer 1 starts flooding the network with fake interest packets with the excluded filter; the queue will begin to saturate as the verification rate is slow as compared to the flooding rate. In the 6th second, Consumer 2 also starts to flood the network; consequently, the queue begins to saturate linearly.
Figure 7: Flooding attack with no threshold value and with two malicious consumers.
Initially, no threshold value is set, and at the 9th-second congestion at the router’s incoming interest packet queue will occur which will result in a drop of other future packets at this router.
Experiment 4 (Scenario 2): with threshold values
In the fourth experiment as shown in Fig. 8, our proposed scheme is enabled at the edge routers in Network Management software. Upon cache miss threshold value reaches 3, it will block the incoming face of Consumer 1 after three failed verification at 4th second. Further, no interest will be received from this malicious consumer face. At 6th second, Malicious Consumer 2 starts to saturate the queue which will, and similarly, after three failed attempts, this face gets blocked as well, and queues start to thrashed after both of the malicious consumer faces are blocked.
Figure 8: Flooding attack with threshold value and with two malicious consumers.
Dynamic threshold value
It is evident in the experiment that with the increase in the Cache_Miss_Ratio, the Queue size will increase because the flooding rate is greater than the verification rate. Also, Cache_Miss has a penality on the processor of the router, which can increase the processing overhead. In the graph (Fig. 9), the initial threshold value is set to buffer size divided by the packet verification rate. At 7th second the queue is filled up to 100%. At this stage, the new packets will start to drop. Here, the system should act prudently and reduce the threshold value to half of the current value, and if flooding continues threshold value is reduced to half as shown in Fig. 10, and so on till the value is reduced to 1. At this stage, the incoming face is blocked as it is considered as an attack. The queue will not be saturated, and memory will be available for other interest packets to get processed.
Figure 9: Special interest packet flooding without dynamic threshold value.
Figure 10: Special interest packet flooding with dynamic threshold value.
If the flooding attack continues, we will multiplicatively decrease the threshold value to another half. This mechanism will continue against that particular flooding malicious face until the threshold value reaches 1. At this stage, that particular face will be blocked and considered as a malicious face. The face will be blocked until the timeout, whose value will be at the network operator’s discretion.
Effectiveness and accuracy of proposed solution by comparing the throughput of the normal special interest packets
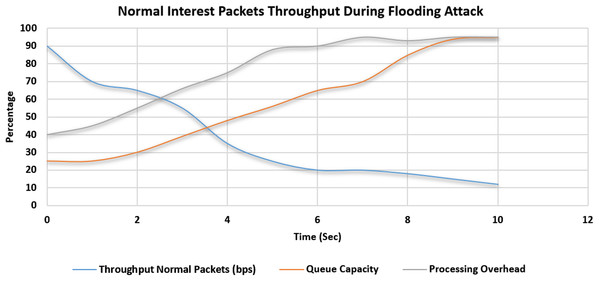
The simulation scenario is depicted in Table 5. In the first scenario, 2,000 malicious interest packets are bombarded by one compromised consumer. A total of 1,000 Normal Interest Packets were also induced in the system by a legitimate consumer in the same domain. In this scenario, no threshold value is set. The maximum throughput of a particular face is 100 bps. Initially, the throughput of the normal interest packets was up to 90% of the total capacity which is the desired result. But in the subsequent seconds, the Malicious packets entered the router. Queue capacity started to saturate, the throughput of the normal interest packet will start to drop as the queue gets filled up with the bombarded malicious packets. The processing overhead also started to increase because of the cost of the cache-miss penalty and verification overhead. This scenario is depicted in Fig. 11. In this second scenario, again 2,000 malicious interest packets are bombarded by one compromised consumer. A total of 1,000 Normal Interest Packets were also induced in the system by a legitimate consumer in the same domain. In this scenario, our proposed solution is placed and activated inside the NDN Router service manager. The maximum throughput of a particular face is 100 bps. The throughput of the normal interest packets was up to 90% of the total capacity which is the desired result. But in the subsequent seconds, the Malicious packets entered the router. Queue capacity started to saturate, then the proposed solution gets activated and blocks the malicious face when the cache miss counter value reached the threshold value. Then we can see that according to our simulation environment after 3rd-second malicious packets didn’t enter the router queue and throughput of the normal interest packet will start to raise and other factors like processing overhead and queue capacity ratio get into the normal working range. This scenario is depicted in Fig. 12. A total of 2,000 Malicious Packets bombarded were detected and dropped successfully by our system. System accuracy proved to be 100%. Also, 1,000 legitimate special Interest packets were processed and no packet was dropped.
| Parameter | Default value |
|---|---|
| Request rate | 100 Interests/second/consumer |
| (special interest packets) | |
| Interest packet max queue length | 500 |
| Verification of interest packet | 25 Interest/second |
| Number of malicious special interest packets | 2,000 pkts |
| Number of normal special interest packets | 1,000 pkts |
| Number of malicious consumers | 1 |
| Threshold value | x |
Figure 11: Throughput of the normal special interest packets in flooding attack scenario.
Figure 12: Throughput of the normal special interest packets in flooding attack scenario with proposed mitigation strategy.
Comparison of throughput, queue capacity and processing overhead during the CPA special interest packet flooding attack and that of our proposed approach is summarized in Table 6.
| Category | Proposed approach | DiBenedetto & Papadopoulos (2016) |
|---|---|---|
| Min throughput of normal interest packet | 65% | 12% |
| Max queue occupation | 55% | 95% |
| Reporting packet size | Lightweight (Sha256 Hash - 32 Bytes) | Heavyweight (complete packet) |
| Trust anchor | Yes | Yes |
| Max processing overhead | 53% | 93% |
| Compromised consumer detection | Yes | Yes |
| Bogus report packet detection | Yes | Partial |
Effectiveness and efficacy of proposed solution by comparing the throughput of interest packets and queue capacity is elaborated in experiments as in Figs. 11 and 12 which is summarized in Table 6. It is evident from the experiments that during the Special Interest Packet flooding attack, our proposed approach showed promising results in terms of throughput, queue capacity and processing overhead.
Conclusion and Future Direction
The main contribution of this work is to devise a mechanism that identifies and prevents the compromised consumers from flooding the network with special Interest packets that are generated during the mitigation process of the Content Poisoning Attack. The compromised consumers place the hash of an un-poisoned content in the excluded filter field of the special interest packet which causes cache miss at the edge router. Owing to the bombardment of these special Interest packets, it will tremendously increase the processing overhead on the NDN Router. The cost is in terms of Cache-Miss penalty and verification overhead. Also, the queue capacity of the NDN Router gets saturated. Consequently, the legitimate requests from the other consumers get dropped or face a substantial amount of delays. We also observed the damaging effect of multiple malicious consumers flooding the edge router which was also well handled by using the proposed technique. After the implementation of our scheme in the Network Service manager at the NDN Edge Router, the malicious face will be blocked when the cache-miss ratio value reaches the specified threshold value. We also have made the threshold value dynamic by adjusting the initial threshold according to cache-miss ratio and queue capacity values. An improvement in this technique can be done by incorporating Quality of Service solutions in NDN Routers. Multiple Virtual queues for special Interest packets can be maintained in NDN Routers to handle the flooding of these packets. Different queuing disciplines and algorithms like Adaptive Virtual Queue (AVQ), Credit-Based Fair Queuing, Weighted Fair Queuing, Quick Fair Queueing, and Class-Based Queuing can be tested to augment our approach. Also, traffic shaping and rate control mechanism can be used to hold back the malicious face.